What is Digital Identity?
Traditionally, a person’s identity is mainly stored and accessed through certified documents: ID cards, passports, birth certificates. It includes names, address details, and a few more identifying features of an entity. In this case, an entity is a person or organization. Digital identity is essentially a digital representation of the information known about the entity. We store it on servers or in the cloud. Digital identity also expands into identifying objects, like computers or software, but this will not be the main topic of this article.
As the world economy is shifting to the web, where we do online shopping, online banking, and use our Email and Social Media accounts on a daily level, the amount of Personal Identifiable Information (PII) increases. This information consists of account logins, passwords, and more detailed insights on our behaviour and interests. It subsequently becomes part of our digital identity. Therefore, it is quite important to understand the critical aspects of Digital Identity Management.
What is Digital Identity Management?
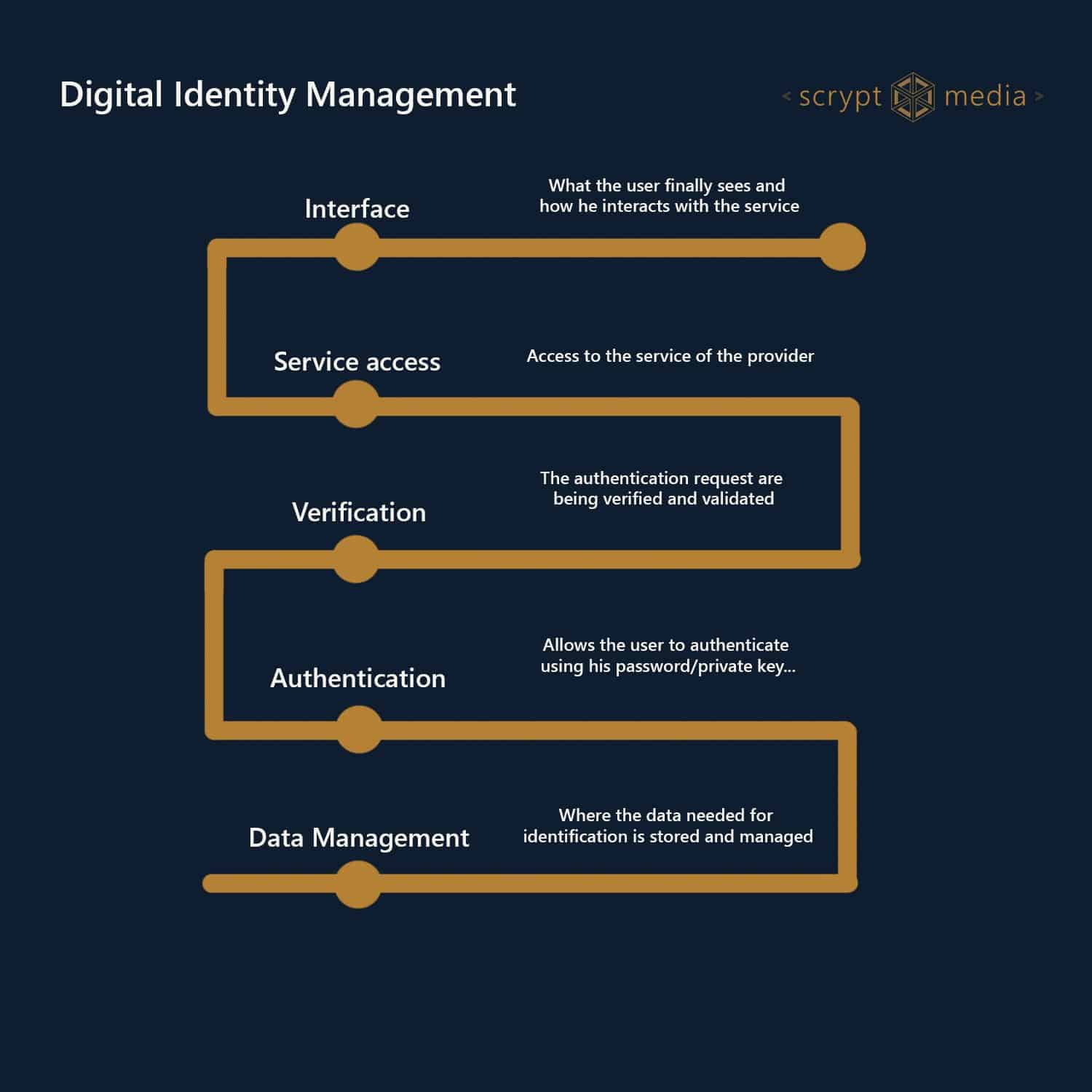
In short, we can summarize Digital Identity Management in 5 different levels:
Data Management
Data Management defines how to store, secure, change, retrieve and archive data about a person. It also needs to define how to delete personal identifiable information.
Authentication
A user provides proof that they are who they claim to be. Examples are a login via password, device or 2-factor authentication, or biometric user authentication via fingerprint or facial recognition.
Verification
The step of verification checks whether provided authentication and proof of identity are valid, and information given is correct and in line with previously stored data.
Access
Access refers to the right of a user to access their account, and the right of a user or third party to access personal identifiable information.
Interface
The user can interact with the service and will see any information relevant to and targeted at his/ her user profile.
The challenges of Digital Identity Management
Trust and Security
People tend to not trust organizations or governments to protect their personal information. A 2017 survey on data privacy and trust found that 68 percent of interviewees across the US and UK do not trust brands to handle their personal information appropriately. This survey also indicates that a majority of people does not trust governments to effectively protect personal data either – 63% of respondents indicate that this should be the concern of individuals.
Security breaches that happened in the past and will happen in the future offer a partial explanation for this lack of trust. According to a Gartner report, by 2020, 60 percent of digital businesses will suffer major service failures due to the inability of IT security teams to manage digital risk, and weak or stolen passwords cause 66% of data breaches. Breaches are up 27% year-over-year.
On the other hand, the anonymity of an online presence makes it also very difficult for a service provider to correctly identify a user, which can be a great risk factor. Providers therefore need to rely on authentication processes that are usually cumbersome and time-consuming for the user, and costly for the organization.
Consent and Control
Apart from data breaches, users are also increasingly concerned about the use of their personal data. In Europe, the GDPR regulation has introduced major guidelines that give end users more control over these aspects. As a result, its implementation in May 2018 has already caused global effects, and other countries will likely follow suit and implement similar regulations.
Ownership
Similar to trust and consent, ownership is a key concern for Digital Identity Management. Who owns personal data? Who owns personal identifiable information, and who can benefit from it? Currently, many internet corporations like Google and Facebook are basing their business models on ads. Other than gaining access to the offered services, end users do not gain any benefit from their data in this model. Apart from the more philosophical question around data ownership, a solution also needs to solve the technical problem of effectively tracking and collecting the value of this data.
Customer Experience
Contrary to a physical identity, the volume of digital identifiers is increasing. Every user has to manage a multitude of accounts, logins, and environments that all hold some personal information. But those environments are rarely connected. As Joseph Lubin of Consensys recently stated at a conference in Paris: “The internet is incomplete. It does not have an identity construct.” The results are a multitude of credentials that users often struggle to manage. A recent survey found that 61% of respondents were using their passwords across multiple sites. This calls for more seamless customer experience and channel integration solutions.
Cost and robustness of infrastructure
Current systems are not robust enough to protect data from being stolen by third parties. Apart from being a security risk, the central storage of large amounts of personal identifiable information also carries a huge price tag of infrastructure cost.
Organizations and governments are acting
Both governments and organizations are working hard to find solutions for these concerns. A multi-stakeholder collaboration on Digital Identity has been launched in January 2018. In this context, Kristalina Georgieva, Chief Executive Officer of the World Bank, announced to secure over $750 million investments in ID-related projects in the next three years. The OECD has recently declared identity and inclusiveness as the top trends in government innovation.
Consequently, it is not surprising that both governments and organizations are considering, or should consider, Blockchain and Distributed Ledger Technology in their quest for Digital Identity solutions.
What makes Blockchain a viable solution?
Imagine you had a way to keep your identity private and securely encrypted, while at the same time letting anyone see that it exists, is valid, and is up to date. If you want to access a new service, you can choose to give the provider access to the necessary details. Those details have been verified by trusted third parties before, but you only had to do that once. So, neither you or the provider are wasting time or money in the process. Here is in more detail how Blockchain can make such a solution work:
Trust and Security
With Blockchain, there is less dependency on one authorising party due to the decentralized nature of the solution. This means that there is no single point of failure.
Consent, Control and Ownership
Cryptographic transactions make is possible to verify the validity of a document or identity without necessarily providing access to specific personal information. Likewise, blockchain enables recording and tracing of transactions in a decentralized manner. These factors make it easier to enable users to control their own personal information, and how that information is used.
Customer Experience
Decentralized data storage along with secure identifiers (public/ private keys) make it much easier to share and exchange access and identity information across platforms. This enables multi-access solutions without risking the security of personal data.
Cost and robustness of infrastructure
Thanks to cryptography and hashing, personal information can still be protected and secured, even if that information, or references to that information, gets stored in a decentralized way. In addition, Blockchain can radically decrease
infrastructure costs for organizations and governments, as it is based on a decentralized network.
Real-life Blockchain use cases for Digital Identity Management
There are different levels at which blockchain can be implemented to provide a solution for Digital Identity Management. The scope and vision of these use cases is increasing from authentication mechanisms to fully self-sovereign ID systems:
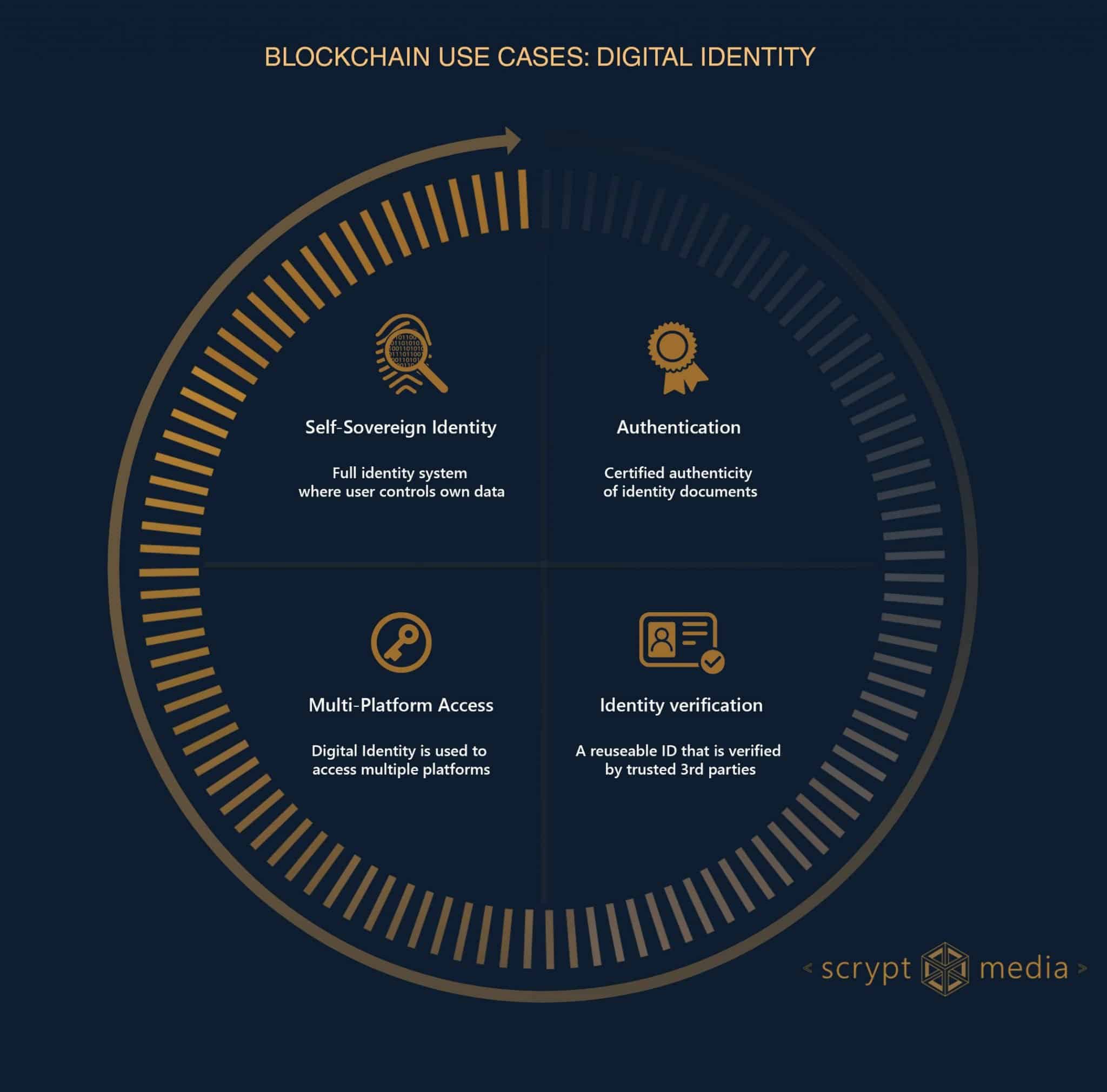
Various projects are currently developing or implementing solutions at each of those levels. Here is a summary of highlights for each level:
Authentication of identity documents
On the lowest level, Blockchain can be used to verify the authenticity of an identity document. This solution uses Blockchain to store and access authentication information, which streamlines the verification process while providing data protection. Two local governments in West Bengal, India, are integrating the application for birth certificates on a blockchain system developed by Lynked.World.
Identity verification
Blockchain-based KYC solutions allow for a streamlined and fast process of identity verification. Historically, KYC is a business process that requires a lot of time and manual or automated labour. Apart from speed, blockchain brings additional security and trust to KYC processes, as the cryptographic signature of a verification can be checked on the blockchain.
IBM is providing blockchain-based KYC solutions as part of the IBM Trusted Identity program.
Civic Reusable KYC is another example of a blockchain-based KYC solution that builds on local storage of user data, along with verification of trusted third parties that provide a reusable proof of identity.
Multi-platform login & access management
Once a user’s identity is verified, that identity should provide access to not only to one, but multiple services. Civic’s Secure Identity Platform uses a verified identity for secure registrations and logins on web and mobile apps without the need for usernames or passwords. A public identifier with hashed identity data is used for the authentication process; a flag indicates whether the data is still valid.
Self-Sovereign Identity – the ultimate Blockchain use case
Above all, the concept of Self-Sovereign Identity is the ultimate level of Blockchain implementation for Digital Identity. Self-Sovereign Identity comes closest to our definition of identity in the offline world: A person is owner of their own identity and can provide proof that this identity is valid. On the Blockchain, proof is provided through decentralized, verifiable credentials. Ultimately, that person can also control the information that is shared, which is the core of the concept of self-sovereignty.
The challenge of implementing a Self-Sovereign Identity system is that it must be widely accepted to provide a real user benefit. While this concept is still in an early development stage, there are a few very interesting examples of Self-Sovereign Identity solutions implemented today:
A Swiss city with a digital ID
Being a haven for Blockchain enthusiasts and developments, the city of Zug (Switzerland) has become one of the first communities worldwide to offer digital identity to their citizens. UPort is the technological solution behind this project.
A progressive government effort
Estonia has proven to be a front runner when it comes to technological innovation. With their e-Estonia program, the country makes public services available to physical (and digital) residents of the country. The e-ID program is providing access to those services.
Striving for a cross-national solution
Veridenkey is another Digital Identity startup that strives to implement Self-Sovereign Identity systems at a broader level. Aiming to build a cross-national identity solution, the team is keeping close contact with government agencies, regulators and trusted institutions, and states to have designed a data architecture that is compliant with EU regulations.
Providing Digital Identities where there were none before
Currently, a large portion of the world population does not have access to digital services, or lost access due to misplacement. BanQu provides an economic identity solution that provides access to transactions for poor, displaced and stateless communities. Their identity solution was piloted with several hundred refugees in Kenya.
UnCHAINed, a recent winner of the Consensys Blockchain for Social Impact incubator, is building a Digital Identity and Resource Allocation System (DIRAS) that aims to help displaced people with both identification and aid distribution.
Identity for all
Sovrin has the ambition to build a global peer-to-peer identity solution, along with governance and trust frameworks that ensure the integrity of their solution. The non-profit organization aims to build a public network, secured and maintained by trusted Stewards. Each individual can establish an identity and link it to various credentials.
Maike Gericke
Maike Gericke is an experienced designer, strategist, innovator and marketer. Her passion for emerging technologies and social / environmental impact led her to start the innovation studio Scrypt with Khalid. Together, they rethink, research, build and teach the use of new technologies for impact.
1 Comment
Comments are closed.

[…] 5: Integrate with secured Digitial Identity solutions where users OWN their personal data. Use and process the data they provide you access to […]